appsec
Found this interesting list: https://list.latio.tech/
On the open source side, there is https://www.dependencytrack.org/
- • 75%
Looking for a new training/certification. People who did OSWA (Web-200 by OffSec), how was it?
www.offsec.com WEB-200: Foundational Web Application Assessments with Kali Linux | OffSecLearn the foundations of web application assessments. Exploit common web vulnerabilities, learn how to exfiltrate sensitive data from target web applications, and earn your OffSec Web Assessor (OSWA) certification.


If you're interested in a way to implement Zero Trust principles like least-privilege access or make your access policies more granular without creating code bloat this is something to check out.
Cerbos Hub externalizes application permissions (RBAC/ABAC) and makes it easier to write and maintain fine-grained access policies without falling into a slow doom spiral of spaghetti code.
You write your policies in a central repo, and deploy as many containerized policy decision points as you need alongside the relevant services in your application. Policy checks are an API call. No single point of failure or lag issues.
You can maintain and monitor distributed policy decision points from one place. Make changes in Hub once and the changes are deployed everywhere. It supports PDPs deployed in serverless environments, at the edge or on device. There's a collaborative policy playground to write and test your policies. It has a central audit log of all the policy decisions that take place across your application.

YouTube Video
Click to view this content.
cross-posted from: https://infosec.pub/post/8123190
> Hello everyone, > > > I work in appsec, my manager would like to send us to a conference this year. We are based in Europe, and the company would like to across intercontinental travel. > > I have OWASP Global 2024 in Lisbon on my radar, as well as the BlackHat EU in London, is there any other conference you guys would recommend?
- • 100%tldrsec.com [tl;dr sec] #215 - Cloud Threat Landscape, Web LLM Security Labs, Azure Logs Primer
A database of cloud security incidents, campaigns, and techniques, Portswigger's labs on testing LLMs in web apps, using Azure logs for detection
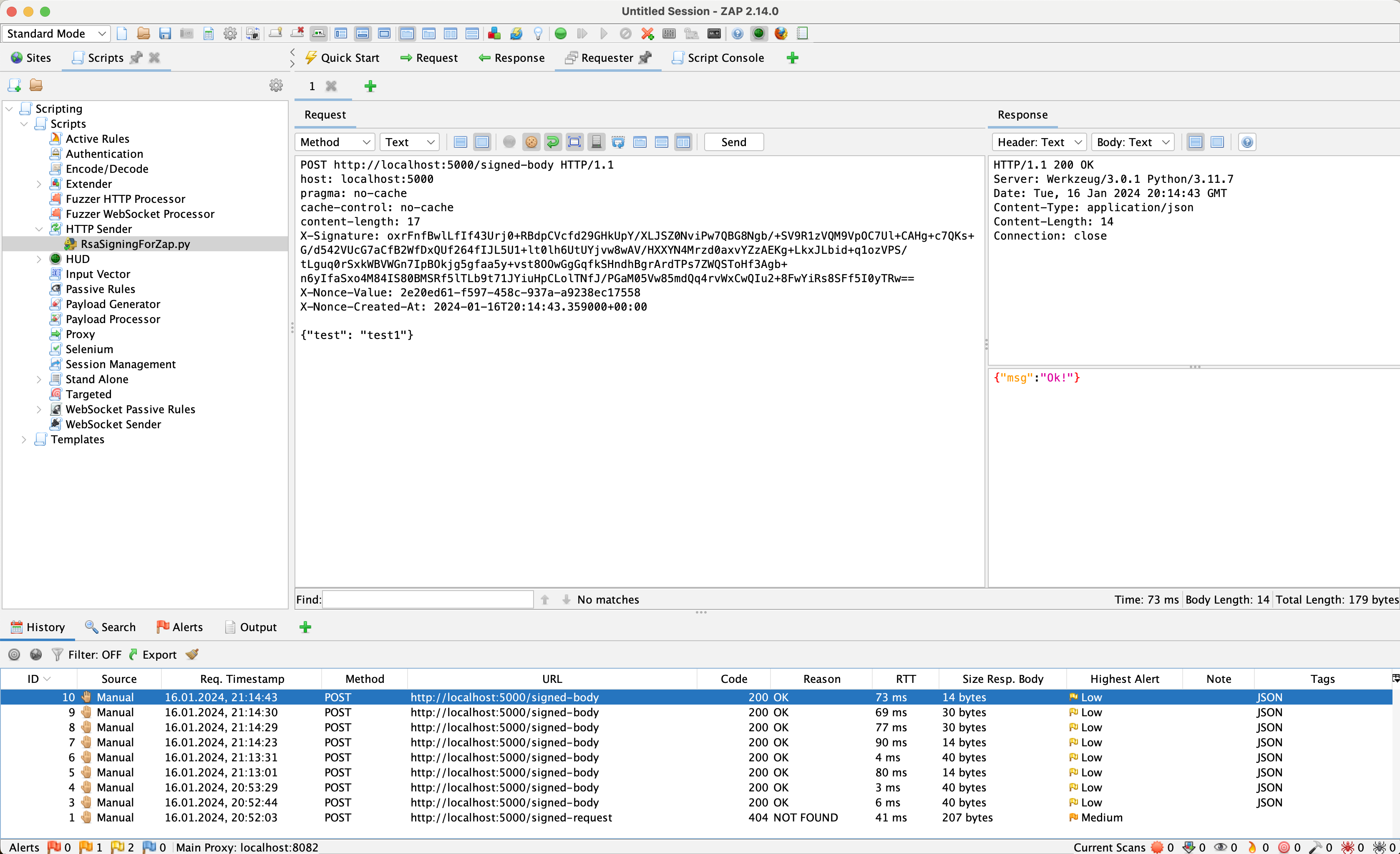
- • 100%www.zaproxy.org Signing Requests using RSA Keys
A new script in the community-scripts repository enables the signing of outgoing requests with RSA keys, addressing the challenge of testing applications that require this functionality.
- • 100%sessionize.com Stir Trek 2024: Call for Speakers
Stir Trek 2024 will take place at the AMC Easton Town Center 30 on Friday, May 3rd. We'll be at the same great location we have been for the past few ...

- owasp.submittable.com OWASP Foundation Submission Manager
OWASP is an open community dedicated to enabling organizations to conceive, develop, acquire, operate, and maintain applications that can be trusted. All of the OWASP tools, documents, forums, and chapters are free and open to anyone interested in improving application security.OWASP is completely v...

- tldrsec.com [tl;dr sec] #213 - AWS Secure Defaults, Damn Vulnerable LLM Agent, cdk-goat
Useful secure defaults + SCPs for your AWS account, a chatbot LLM ReAct agent for prompt injection practice, vulnerable by design AWS Cloud Development Kit infrastructure
- • 100%appsec.beehiiv.com Reasonable 🔐AppSec #33 - Signing Off '23 with a Bang: Five Security Articles, AppSec New Year's Resolutions, and Podcast Corner
A review of application security happenings and industry news from Chris Romeo.

- • 100%owasp.org Trustwave Transfers ModSecurity Custodianship to OWASP | OWASP Foundation
Trustwave Transfers ModSecurity Custodianship to OWASP on the main website for The OWASP Foundation. OWASP is a nonprofit foundation that works to improve the security of software.

- • 100%blog.solidsnail.com npm search RCE? - Escape Sequence Injection
How many programmers does it take to filter out 36 characters? You may think this is an opening to a joke, but it’s not.

- • 100%blog.solidsnail.com It’s not a Feature, It’s a Vulnerability
It takes a special kind of person to name a company after their own body part. Fortunately the Microsoft Security Response Center doesn’t seem to have inherited that kind of mentality, because when I have reported not a bug but a feature as a vulnerability - they accepted it.
cross-posted from: https://infosec.pub/post/5707149
> I talk about a report I've made to MSRC in the beginning of the year regarding vscode. > > It's a bit different. There's no in depth technical stuff, because I basically just reported the feature, not a bug.
- • 100%www.theregister.com GitHub Copilot, Amazon Code Whisperer emit people's API keys
AI dev assistants can be convinced to spill secrets learned during training

- • 100%blog.solidsnail.com From Terminal Output to Arbitrary Remote Code Execution
It was the year of the Linux desktop 1978. Old yellowed computers were not yet old, nor yellowed. Digital Equipment Corporation released the first popular terminal to support a standardized in-band encoding for control functions, the VT100.
This is my first write-up, on a vulnerability I discovered in iTerm2 (RCE). Would love to hear opinions on this. I tried to make the writing engaging.
- cheatsheetseries.owasp.org Mobile Application Security - OWASP Cheat Sheet Series
Website with the collection of all the cheat sheets of the project.
Mobile Application Security Cheat Sheet
Mobile application development presents certain security challenges that are unique compared to web applications and other forms of software. This cheat sheet provides guidance on security considerations for mobile app development. It is not a comprehensive guide by any means, but rather a starting point for developers to consider security in their mobile app development.
Architecture & Design
1. Secure by Design
...
- owasp.org OWASP Top 10 for Large Language Model Applications | OWASP Foundation
Aims to educate developers, designers, architects, managers, and organizations about the potential security risks when deploying and managing Large Language Models (LLMs)

- • 100%www.bleepingcomputer.com Google Cloud Build bug lets hackers launch supply chain attacks
A critical design flaw in the Google Cloud Build service discovered by cloud security firm Orca Security can let attackers escalate privileges, providing them with almost nearly-full and unauthorized access to Google Artifact Registry code repositories.

- • 100%portswigger.net Exploiting XSS in hidden inputs and meta tags
In this post we are going to show how you can (ab)use the new HTML popup functionality in Chrome to exploit XSS in meta tags and hidden inputs. It all started when I noticed the new popover behaviour

- • 100%www.osohq.com Why Authorization is Hard
There's a fundamental tension in authorization. Is it business logic or authorization logic? Should it be in the app, or separate? Let’s talk about what makes a

- • 100%www.darkreading.com ChatGPT Hallucinations Open Developers to Supply Chain Malware Attacks
Attackers could exploit a common AI experience — false recommendations — to spread malicious code via developers that use ChatGPT to create software.
- • 100%www.reversinglabs.com Here’s MITRE’s top-25 CWE list — with your old vulnerability category favorites
C’mon, dev teams — it's about time to get serious about memory safety, XSS and SQLi.

- portswigger.net GraphQL API vulnerabilities | Web Security Academy
GraphQL vulnerabilities generally arise due to implementation and design flaws. For example, the introspection feature may be left active, enabling ...

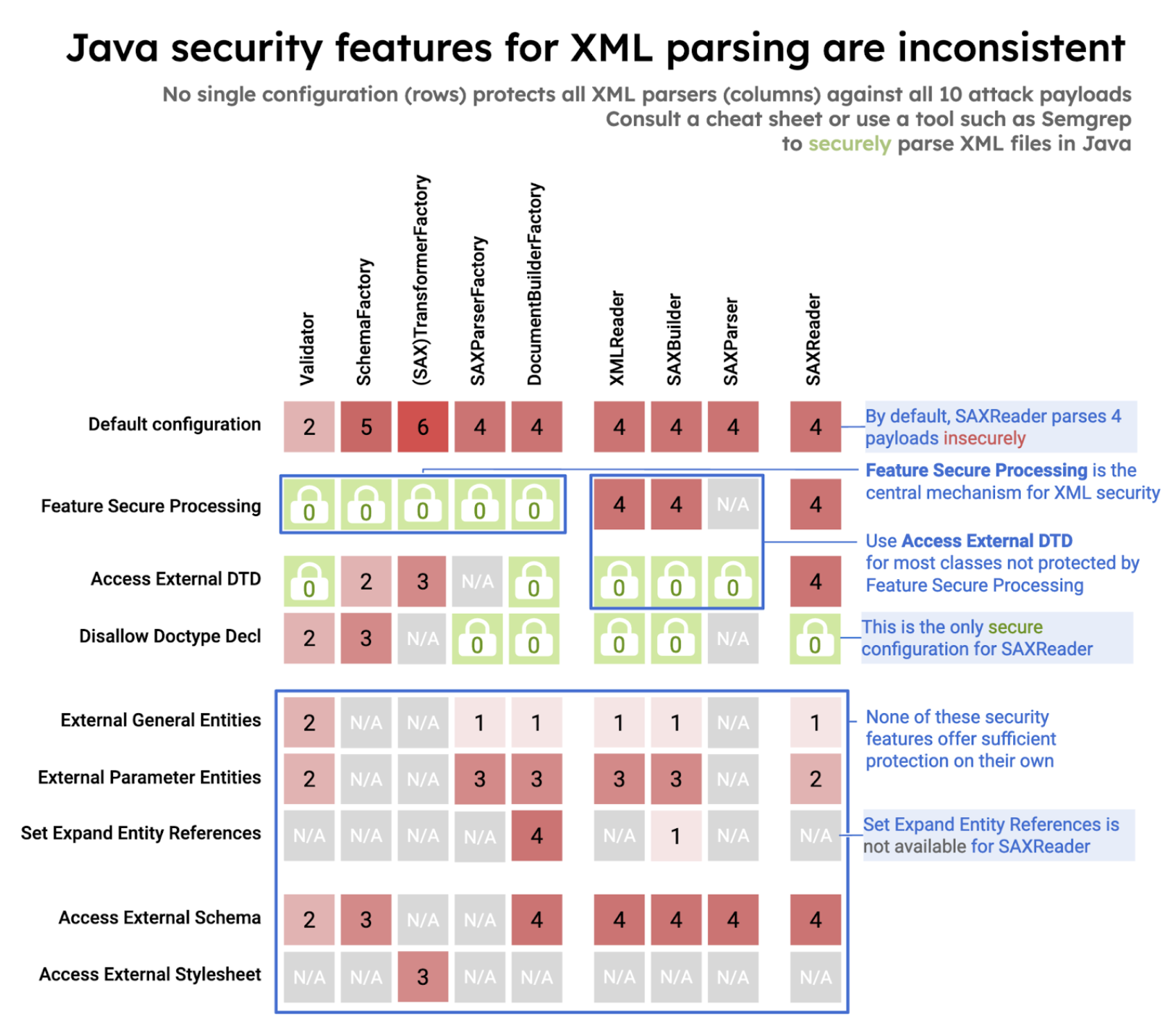
- • 100%semgrep.dev XML Security in Java
In this blog post, you can read just how much of a mess Java XML security is
- • 100%tldrsec.com Cache Me If You Can: Messing with Web Caching
In this talk, Louis covers 3 web cache related attacks: cache deception, edge side includes, and cache poisoning.

- • 100%
AppSec podcasts?
There is a nice list of Infosec podcasts here: https://infosec.pub/post/152754
What are your more specialized appsec recommendations?
- • 100%sec-consult.com DNS Analyzer - Finding DNS vulnerabilities with Burp Suite
A brand-new Burp Suite extension for discovering DNS vulnerabilities in web applications.
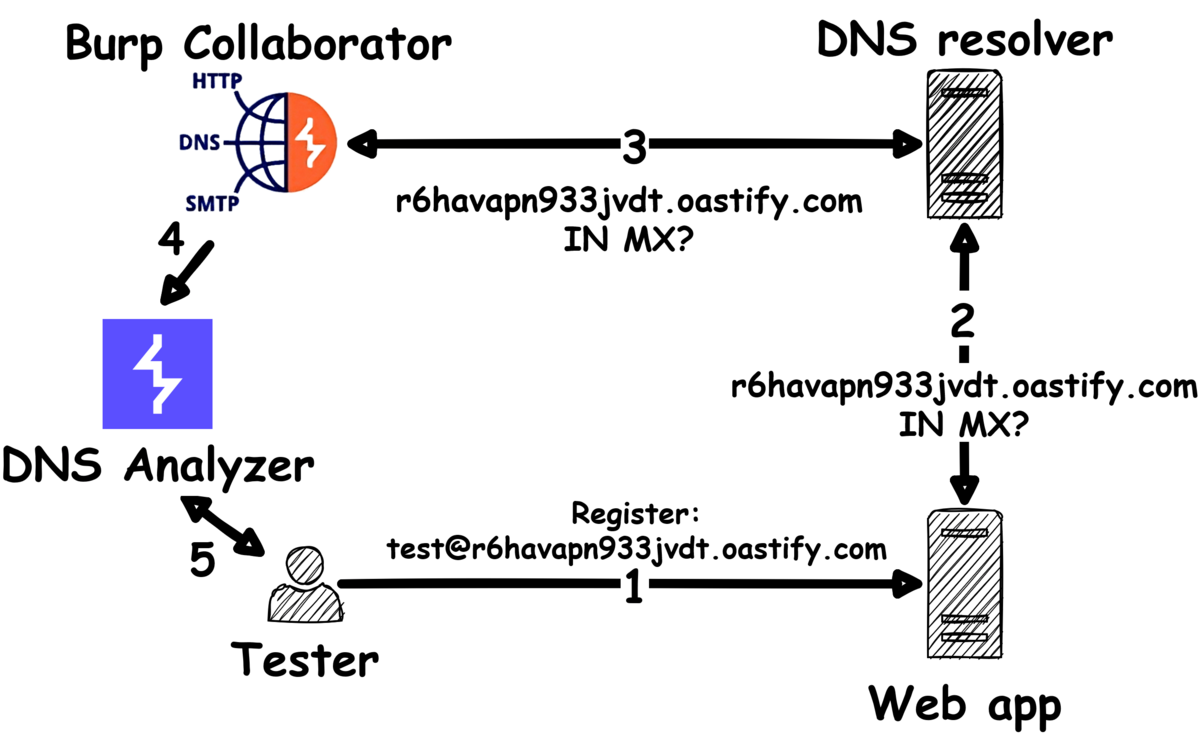
A brand-new Burp Suite extension for discovering DNS vulnerabilities in web applications.
- • 100%portswigger.net Bypassing CSP via DOM clobbering
You might have found HTML injection, but unfortunately identified that the site is protected with CSP. All is not lost, it might be possible to bypass CSP using DOM clobbering, which you can now detec

You might have found HTML injection, but unfortunately identified that the site is protected with CSP. All is not lost, it might be possible to bypass CSP using DOM clobbering, which you can now detect using DOM Invader! In this post we’ll show you how.
We’ve based the test case on a bug bounty site, so you’re likely to encounter similar code in the wild. If you’re unfamiliar with DOM clobbering then head over to our Academy to learn about this attack class and solve the labs.
- summoning.team Summoning Team
Pre-authenticated RCE in VMware vRealize Network Insight (CVE-2023-20887)

