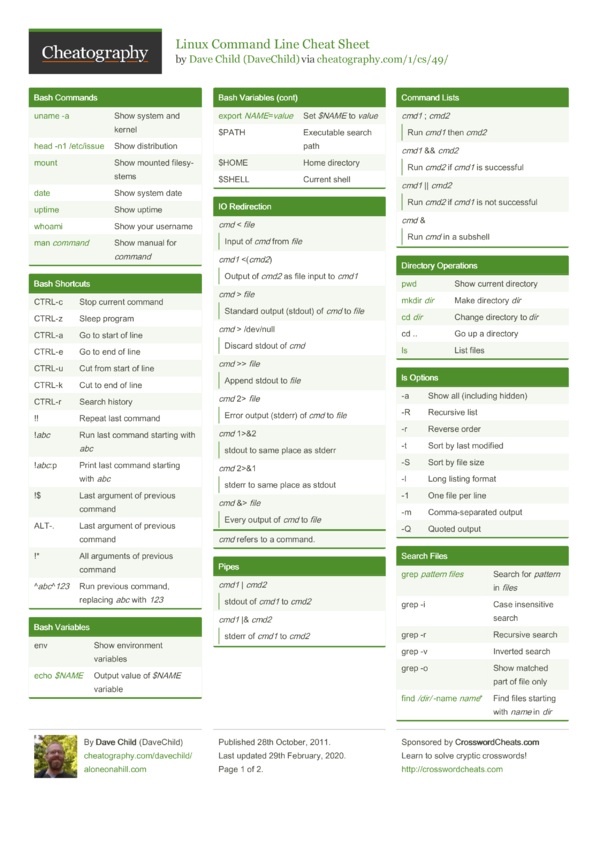
Nice initiative.
Yea, I have submitted multiple abuse emails with details to domain registrars for scamming and phishing.
Didn’t receive any update from them on any action taken yet.
In this tutorial, we will explore how to use sed (stream editor) with examples in the Markdown language. sed is a powerful command-line tool for text manipulation and is widely used for tasks such as search and replace, line filtering, and text transformations. What is described below barely scratches the surface what sed can do.
Table of Contents
- Installing Sed
- Basic Usage
- Search and Replace
- Deleting Lines
- Inserting and Appending Text
- Transformations
- Working with Files
- Conclusion
1. Installing Sed
Before we begin, make sure sed is installed on your system. It usually comes pre-installed on Unix-like systems (e.g., Linux, macOS). To check if sed is installed, open your terminal and run the following command:
sed --version
If sed is not installed, you can install it using your package manager. For example, on Ubuntu or Debian-based systems, you can use the following command:
sudo apt-get install sed
2. Basic Usage
To use sed, you need to provide it with a command and the input text to process. The basic syntax is as follows:
sed 'command' input.txt
Here, 'command' represents the action you want to perform on the input text. It can be a search pattern, a substitution, or a transformation. input.txt is the file containing the text to process. If you omit the file name, sed will read from the standard input.
3. Search and Replace
One of the most common tasks with sed is search and replace. To substitute a pattern with another in Markdown files, use the s command. The basic syntax is:
sed 's/pattern/replacement/' input.md
For example, to replace all occurrences of the word "apple" with "orange" in input.md, use the following command:
sed 's/apple/orange/' input.md
4. Deleting Lines
You can also delete specific lines from a Markdown file using sed. The d command is used to delete lines that match a particular pattern. The syntax is as follows:
sed '/pattern/d' input.md
For example, to delete all lines containing the word "banana" from input.md, use the following command:
sed '/banana/d' input.md
5. Inserting and Appending Text
sed allows you to insert or append text at specific locations in a Markdown file. The i command is used to insert text before a line, and the a command is used to append text after a line. The syntax is as follows:
sed '/pattern/i\inserted text' input.md sed '/pattern/a\appended text' input.md
For example, to insert the line "This is a new paragraph." before the line containing the word "example" in input.md, use the following command:
sed '/example/i\This is a new paragraph.' input.md
6. Transformations
sed provides various transformation commands that can be used to modify Markdown files. Some useful commands include:
-
y: Transliterate characters. For example, to convert all uppercase letters to lowercase, use:sed 'y/ABCDEFGHIJKLMNOPQRSTUVWXYZ/abcdefghijklmnopqrstuvwxyz/' input.md -
p: Print lines. By default,sedonly prints the modified lines. To print all lines, use:sed -n 'p' input.md -
r: Read and insert the contents of a file. For example, to insert the contents ofinsert.mdafter the line containing the word "insertion point" ininput.md, use:sed '/insertion point/r insert.md' input.md
These are just a few examples of the transformation commands available in sed.
7. Working with Files
By default, sed modifies the input in-place. To make changes to a file and save the output to a new file, you can use input/output redirection:
sed 'command' input.md > output.md
This command runs sed on input.md and saves the output to output.md. Be cautious when using redirection, as it will overwrite the contents of output.md if it already exists.
8. Conclusion
In this tutorial, we have explored the basics of using sed with Markdown files. You have learned how to perform search and replace operations, delete lines, insert and append text, apply transformations, and work with files. sed offers a wide range of capabilities, and with practice, you can become proficient in manipulating Markdown files using this powerful tool.
cross-posted from: https://lemmy.run/post/19113
> In this tutorial, we will walk through the process of using the grep command to filter Nginx logs based on a given time range. grep is a powerful command-line tool for searching and filtering text patterns in files.
>
> Step 1: Access the Nginx Log Files
> First, access the server or machine where Nginx is running. Locate the log files that you want to search. Typically, Nginx log files are located in the /var/log/nginx/ directory. The main log file is usually named access.log. You may have additional log files for different purposes, such as error logging.
>
> Step 2: Understanding Nginx Log Format
> To effectively search through Nginx logs, it is essential to understand the log format. By default, Nginx uses the combined log format, which consists of several fields, including the timestamp. The timestamp format varies depending on your Nginx configuration but is usually in the following format: [day/month/year:hour:minute:second timezone].
>
> Step 3: Determine the Time Range
> Decide on the time range you want to filter. You will need to provide the starting and ending timestamps in the log format mentioned earlier. For example, if you want to filter logs between June 24th, 2023, from 10:00 AM to 12:00 PM, the time range would be [24/Jun/2023:10:00:00 and [24/Jun/2023:12:00:00.
>
> Step 4: Use Grep to Filter Logs
> With the log files and time range identified, you can now use grep to filter the logs. Open a terminal or SSH session to the server and execute the following command:
>
> bash > grep "\[24/Jun/2023:10:00:" /var/log/nginx/access.log | awk '$4 >= "[24/Jun/2023:10:00:" && $4 <= "[24/Jun/2023:12:00:"' >
>
> Replace starting_timestamp and ending_timestamp with the appropriate timestamps you determined in Step 3. The grep command searches for lines containing the starting timestamp in the log file specified (access.log in this example). The output is then piped (|) to awk, which filters the logs based on the time range.
>
> Step 5: View Filtered Logs
> After executing the command, you should see the filtered logs that fall within the specified time range. The output will include the entire log lines matching the filter.
>
> Additional Tips:
> - If you have multiple log files, you can either specify them individually in the grep command or use a wildcard character (*) to match all files in the directory.
> - You can redirect the filtered output to a file by appending > output.log at the end of the command. This will create a file named output.log containing the filtered logs.
>
> That's it! You have successfully filtered Nginx logs using grep based on a given time range. Feel free to explore additional options and features of grep to further refine your log analysis.
cross-posted from: https://lemmy.run/post/19113
> In this tutorial, we will walk through the process of using the grep command to filter Nginx logs based on a given time range. grep is a powerful command-line tool for searching and filtering text patterns in files.
>
> Step 1: Access the Nginx Log Files
> First, access the server or machine where Nginx is running. Locate the log files that you want to search. Typically, Nginx log files are located in the /var/log/nginx/ directory. The main log file is usually named access.log. You may have additional log files for different purposes, such as error logging.
>
> Step 2: Understanding Nginx Log Format
> To effectively search through Nginx logs, it is essential to understand the log format. By default, Nginx uses the combined log format, which consists of several fields, including the timestamp. The timestamp format varies depending on your Nginx configuration but is usually in the following format: [day/month/year:hour:minute:second timezone].
>
> Step 3: Determine the Time Range
> Decide on the time range you want to filter. You will need to provide the starting and ending timestamps in the log format mentioned earlier. For example, if you want to filter logs between June 24th, 2023, from 10:00 AM to 12:00 PM, the time range would be [24/Jun/2023:10:00:00 and [24/Jun/2023:12:00:00.
>
> Step 4: Use Grep to Filter Logs
> With the log files and time range identified, you can now use grep to filter the logs. Open a terminal or SSH session to the server and execute the following command:
>
> bash > grep "\[24/Jun/2023:10:00:" /var/log/nginx/access.log | awk '$4 >= "[24/Jun/2023:10:00:" && $4 <= "[24/Jun/2023:12:00:"' >
>
> Replace starting_timestamp and ending_timestamp with the appropriate timestamps you determined in Step 3. The grep command searches for lines containing the starting timestamp in the log file specified (access.log in this example). The output is then piped (|) to awk, which filters the logs based on the time range.
>
> Step 5: View Filtered Logs
> After executing the command, you should see the filtered logs that fall within the specified time range. The output will include the entire log lines matching the filter.
>
> Additional Tips:
> - If you have multiple log files, you can either specify them individually in the grep command or use a wildcard character (*) to match all files in the directory.
> - You can redirect the filtered output to a file by appending > output.log at the end of the command. This will create a file named output.log containing the filtered logs.
>
> That's it! You have successfully filtered Nginx logs using grep based on a given time range. Feel free to explore additional options and features of grep to further refine your log analysis.
cross-posted from: https://lemmy.run/post/15922
> # Running Commands in Parallel in Linux
>
> In Linux, you can execute multiple commands simultaneously by running them in parallel. This can help improve the overall execution time and efficiency of your tasks. In this tutorial, we will explore different methods to run commands in parallel in a Linux environment.
>
> ## Method 1: Using & (ampersand) symbol
>
> The simplest way to run commands in parallel is by appending the & symbol at the end of each command. Here's how you can do it:
>
> bash > command_1 & command_2 & command_3 & >
>
> This syntax allows each command to run in the background, enabling parallel execution. The shell will immediately return the command prompt, and the commands will execute concurrently.
>
> For example, to compress three different files in parallel using the gzip command:
>
> bash > gzip file1.txt & gzip file2.txt & gzip file3.txt & >
>
> ## Method 2: Using xargs with -P option
>
> The xargs command is useful for building and executing commands from standard input. By utilizing its -P option, you can specify the maximum number of commands to run in parallel. Here's an example:
>
> bash > echo -e "command_1\ncommand_2\ncommand_3" | xargs -P 3 -I {} sh -c "{}" & >
>
> In this example, we use the echo command to generate a list of commands separated by newline characters. This list is then piped (|) to xargs, which executes each command in parallel. The -P 3 option indicates that a maximum of three commands should run concurrently. Adjust the number according to your requirements.
>
> For instance, to run three different wget commands in parallel to download files:
>
> bash > echo -e "wget http://example.com/file1.txt\nwget http://example.com/file2.txt\nwget http://example.com/file3.txt" | xargs -P 3 -I {} sh -c "{}" & >
>
> ## Method 3: Using GNU Parallel
>
> GNU Parallel is a powerful tool specifically designed to run jobs in parallel. It provides extensive features and flexibility. To use GNU Parallel, follow these steps:
>
> 1. Install GNU Parallel if it's not already installed. You can typically find it in your Linux distribution's package manager.
> 2. Create a file (e.g., commands.txt) and add one command per line:
>
> plaintext > command_1 > command_2 > command_3 >
>
> 3. Run the following command to execute the commands in parallel:
>
> bash > parallel -j 3 < commands.txt >
>
> The -j 3 option specifies the maximum number of parallel jobs to run. Adjust it according to your needs.
>
> For example, if you have a file called urls.txt containing URLs and you want to download them in parallel using wget:
>
> bash > parallel -j 3 wget {} < urls.txt >
>
> GNU Parallel also offers numerous advanced options for complex parallel job management. Refer to its documentation for further information.
>
> ## Conclusion
>
> Running commands in parallel can significantly speed up your tasks by utilizing the available resources efficiently. In this tutorial, you've learned three methods for running commands in parallel in Linux:
>
> 1. Using the & symbol to run commands in the background.
> 2. Utilizing xargs with the -P option to define the maximum parallelism.
> 3. Using GNU Parallel for advanced parallel job management.
>
> Choose the method that best suits your requirements and optimize your workflow by executing commands concurrently.
cross-posted from: https://lemmy.run/post/15922
> # Running Commands in Parallel in Linux
>
> In Linux, you can execute multiple commands simultaneously by running them in parallel. This can help improve the overall execution time and efficiency of your tasks. In this tutorial, we will explore different methods to run commands in parallel in a Linux environment.
>
> ## Method 1: Using & (ampersand) symbol
>
> The simplest way to run commands in parallel is by appending the & symbol at the end of each command. Here's how you can do it:
>
> bash > command_1 & command_2 & command_3 & >
>
> This syntax allows each command to run in the background, enabling parallel execution. The shell will immediately return the command prompt, and the commands will execute concurrently.
>
> For example, to compress three different files in parallel using the gzip command:
>
> bash > gzip file1.txt & gzip file2.txt & gzip file3.txt & >
>
> ## Method 2: Using xargs with -P option
>
> The xargs command is useful for building and executing commands from standard input. By utilizing its -P option, you can specify the maximum number of commands to run in parallel. Here's an example:
>
> bash > echo -e "command_1\ncommand_2\ncommand_3" | xargs -P 3 -I {} sh -c "{}" & >
>
> In this example, we use the echo command to generate a list of commands separated by newline characters. This list is then piped (|) to xargs, which executes each command in parallel. The -P 3 option indicates that a maximum of three commands should run concurrently. Adjust the number according to your requirements.
>
> For instance, to run three different wget commands in parallel to download files:
>
> bash > echo -e "wget http://example.com/file1.txt\nwget http://example.com/file2.txt\nwget http://example.com/file3.txt" | xargs -P 3 -I {} sh -c "{}" & >
>
> ## Method 3: Using GNU Parallel
>
> GNU Parallel is a powerful tool specifically designed to run jobs in parallel. It provides extensive features and flexibility. To use GNU Parallel, follow these steps:
>
> 1. Install GNU Parallel if it's not already installed. You can typically find it in your Linux distribution's package manager.
> 2. Create a file (e.g., commands.txt) and add one command per line:
>
> plaintext > command_1 > command_2 > command_3 >
>
> 3. Run the following command to execute the commands in parallel:
>
> bash > parallel -j 3 < commands.txt >
>
> The -j 3 option specifies the maximum number of parallel jobs to run. Adjust it according to your needs.
>
> For example, if you have a file called urls.txt containing URLs and you want to download them in parallel using wget:
>
> bash > parallel -j 3 wget {} < urls.txt >
>
> GNU Parallel also offers numerous advanced options for complex parallel job management. Refer to its documentation for further information.
>
> ## Conclusion
>
> Running commands in parallel can significantly speed up your tasks by utilizing the available resources efficiently. In this tutorial, you've learned three methods for running commands in parallel in Linux:
>
> 1. Using the & symbol to run commands in the background.
> 2. Utilizing xargs with the -P option to define the maximum parallelism.
> 3. Using GNU Parallel for advanced parallel job management.
>
> Choose the method that best suits your requirements and optimize your workflow by executing commands concurrently.
cross-posted from: https://lemmy.run/post/10868
> # Beginner's Guide to grep
>
> grep is a powerful command-line tool used for searching and filtering text in files. It allows you to find specific patterns or strings within files, making it an invaluable tool for developers, sysadmins, and anyone working with text data. In this guide, we will cover the basics of using grep and provide you with some useful examples to get started.
>
> ## Installation
>
> grep is a standard utility on most Unix-like systems, including Linux and macOS. If you're using a Windows operating system, you can install it by using the Windows Subsystem for Linux (WSL) or through tools like Git Bash, Cygwin, or MinGW.
>
> ## Basic Usage
>
> The basic syntax of grep is as follows:
>
> > grep [options] pattern [file(s)] >
>
> - options: Optional flags that modify the behavior of grep.
> - pattern: The pattern or regular expression to search for.
> - file(s): Optional file(s) to search within. If not provided, grep will read from standard input.
>
> ## Examples
>
> ### Searching in a Single File
>
> To search for a specific pattern in a single file, use the following command:
>
> bash > grep "pattern" file.txt >
>
> Replace "pattern" with the text you want to search for and file.txt with the name of the file you want to search in.
>
> ### Searching in Multiple Files
>
> If you want to search for a pattern across multiple files, use the following command:
>
> bash > grep "pattern" file1.txt file2.txt file3.txt >
>
> You can specify as many files as you want, separating them with spaces.
>
> ### Ignoring Case
>
> By default, grep is case-sensitive. To perform a case-insensitive search, use the -i option:
>
> bash > grep -i "pattern" file.txt >
>
> ### Displaying Line Numbers
>
> To display line numbers along with the matching lines, use the -n option:
>
> bash > grep -n "pattern" file.txt >
>
> This can be helpful when you want to know the line numbers where matches occur.
>
> ### Searching Recursively
>
> To search for a pattern in all files within a directory and its subdirectories, use the -r option (recursive search):
>
> bash > grep -r "pattern" directory/ >
>
> Replace directory/ with the path to the directory you want to search in.
>
> ### Using Regular Expressions
>
> grep supports regular expressions for more advanced pattern matching. Here's an example using a regular expression to search for email addresses:
>
> bash > grep -E "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}\b" file.txt >
>
> In this case, the -E option enables extended regular expressions.
>
> ## Conclusion
>
> grep is a versatile tool that can greatly enhance your text searching and filtering capabilities. With the knowledge you've gained in this beginner's guide, you can start using grep to quickly find and extract the information you need from text files. Experiment with different options and explore more advanced regular expressions to further expand your skills with grep. Happy grepping!
cross-posted from: https://lemmy.run/post/10868
> # Beginner's Guide to grep
>
> grep is a powerful command-line tool used for searching and filtering text in files. It allows you to find specific patterns or strings within files, making it an invaluable tool for developers, sysadmins, and anyone working with text data. In this guide, we will cover the basics of using grep and provide you with some useful examples to get started.
>
> ## Installation
>
> grep is a standard utility on most Unix-like systems, including Linux and macOS. If you're using a Windows operating system, you can install it by using the Windows Subsystem for Linux (WSL) or through tools like Git Bash, Cygwin, or MinGW.
>
> ## Basic Usage
>
> The basic syntax of grep is as follows:
>
> > grep [options] pattern [file(s)] >
>
> - options: Optional flags that modify the behavior of grep.
> - pattern: The pattern or regular expression to search for.
> - file(s): Optional file(s) to search within. If not provided, grep will read from standard input.
>
> ## Examples
>
> ### Searching in a Single File
>
> To search for a specific pattern in a single file, use the following command:
>
> bash > grep "pattern" file.txt >
>
> Replace "pattern" with the text you want to search for and file.txt with the name of the file you want to search in.
>
> ### Searching in Multiple Files
>
> If you want to search for a pattern across multiple files, use the following command:
>
> bash > grep "pattern" file1.txt file2.txt file3.txt >
>
> You can specify as many files as you want, separating them with spaces.
>
> ### Ignoring Case
>
> By default, grep is case-sensitive. To perform a case-insensitive search, use the -i option:
>
> bash > grep -i "pattern" file.txt >
>
> ### Displaying Line Numbers
>
> To display line numbers along with the matching lines, use the -n option:
>
> bash > grep -n "pattern" file.txt >
>
> This can be helpful when you want to know the line numbers where matches occur.
>
> ### Searching Recursively
>
> To search for a pattern in all files within a directory and its subdirectories, use the -r option (recursive search):
>
> bash > grep -r "pattern" directory/ >
>
> Replace directory/ with the path to the directory you want to search in.
>
> ### Using Regular Expressions
>
> grep supports regular expressions for more advanced pattern matching. Here's an example using a regular expression to search for email addresses:
>
> bash > grep -E "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}\b" file.txt >
>
> In this case, the -E option enables extended regular expressions.
>
> ## Conclusion
>
> grep is a versatile tool that can greatly enhance your text searching and filtering capabilities. With the knowledge you've gained in this beginner's guide, you can start using grep to quickly find and extract the information you need from text files. Experiment with different options and explore more advanced regular expressions to further expand your skills with grep. Happy grepping!
Beginner's Guide to grep
grep is a powerful command-line tool used for searching and filtering text in files. It allows you to find specific patterns or strings within files, making it an invaluable tool for developers, sysadmins, and anyone working with text data. In this guide, we will cover the basics of using grep and provide you with some useful examples to get started.
Installation
grep is a standard utility on most Unix-like systems, including Linux and macOS. If you're using a Windows operating system, you can install it by using the Windows Subsystem for Linux (WSL) or through tools like Git Bash, Cygwin, or MinGW.
Basic Usage
The basic syntax of grep is as follows:
grep [options] pattern [file(s)]
options: Optional flags that modify the behavior ofgrep.pattern: The pattern or regular expression to search for.file(s): Optional file(s) to search within. If not provided,grepwill read from standard input.
Examples
Searching in a Single File
To search for a specific pattern in a single file, use the following command:
bash grep "pattern" file.txt
Replace "pattern" with the text you want to search for and file.txt with the name of the file you want to search in.
Searching in Multiple Files
If you want to search for a pattern across multiple files, use the following command:
bash grep "pattern" file1.txt file2.txt file3.txt
You can specify as many files as you want, separating them with spaces.
Ignoring Case
By default, grep is case-sensitive. To perform a case-insensitive search, use the -i option:
bash grep -i "pattern" file.txt
Displaying Line Numbers
To display line numbers along with the matching lines, use the -n option:
bash grep -n "pattern" file.txt
This can be helpful when you want to know the line numbers where matches occur.
Searching Recursively
To search for a pattern in all files within a directory and its subdirectories, use the -r option (recursive search):
bash grep -r "pattern" directory/
Replace directory/ with the path to the directory you want to search in.
Using Regular Expressions
grep supports regular expressions for more advanced pattern matching. Here's an example using a regular expression to search for email addresses:
bash grep -E "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,}\b" file.txt
In this case, the -E option enables extended regular expressions.
Conclusion
grep is a versatile tool that can greatly enhance your text searching and filtering capabilities. With the knowledge you've gained in this beginner's guide, you can start using grep to quickly find and extract the information you need from text files. Experiment with different options and explore more advanced regular expressions to further expand your skills with grep. Happy grepping!
cross-posted from: https://lemmy.run/post/10475
> ## Testing Service Accounts in Kubernetes
>
> Service accounts in Kubernetes are used to provide a secure way for applications and services to authenticate and interact with the Kubernetes API. Testing service accounts ensures their functionality and security. In this guide, we will explore different methods to test service accounts in Kubernetes.
>
> ### 1. Verifying Service Account Existence
>
> To start testing service accounts, you first need to ensure they exist in your Kubernetes cluster. You can use the following command to list all the available service accounts:
>
> bash > kubectl get serviceaccounts >
>
> Verify that the service account you want to test is present in the output. If it's missing, you may need to create it using a YAML manifest or the kubectl create serviceaccount command.
>
> ### 2. Checking Service Account Permissions
>
> After confirming the existence of the service account, the next step is to verify its permissions. Service accounts in Kubernetes are associated with roles or cluster roles, which define what resources and actions they can access.
>
> To check the permissions of a service account, you can use the kubectl auth can-i command. For example, to check if a service account can create pods, run:
>
> bash > kubectl auth can-i create pods --as=system:serviceaccount:<namespace>:<service-account> >
>
> Replace <namespace> with the desired namespace and <service-account> with the name of the service account.
>
> ### 3. Testing Service Account Authentication
>
> Service accounts authenticate with the Kubernetes API using bearer tokens. To test service account authentication, you can manually retrieve the token associated with the service account and use it to authenticate requests.
>
> To get the token for a service account, run:
>
> bash > kubectl get secret <service-account-token-secret> -o jsonpath="{.data.token}" | base64 --decode >
>
> Replace <service-account-token-secret> with the actual name of the secret associated with the service account. This command decodes and outputs the service account token.
>
> You can then use the obtained token to authenticate requests to the Kubernetes API, for example, by including it in the Authorization header using tools like curl or writing a simple program.
>
> ### 4. Testing Service Account RBAC Policies
>
> Role-Based Access Control (RBAC) policies govern the access permissions for service accounts. It's crucial to test these policies to ensure service accounts have the appropriate level of access.
>
> One way to test RBAC policies is by creating a Pod that uses the service account you want to test and attempting to perform actions that the service account should or shouldn't be allowed to do. Observe the behavior and verify if the access is granted or denied as expected.
>
> ### 5. Automated Testing
>
> To streamline the testing process, you can create automated tests using testing frameworks and tools specific to Kubernetes. For example, the Kubernetes Test Framework (KTF) provides a set of libraries and utilities for writing tests for Kubernetes components, including service accounts.
>
> Using such frameworks allows you to write comprehensive test cases to validate service account behavior, permissions, and RBAC policies automatically.
>
> ### Conclusion
>
> Testing service accounts in Kubernetes ensures their proper functioning and adherence to security policies. By verifying service account existence, checking permissions, testing authentication, and validating RBAC policies, you can confidently use and rely on service accounts in your Kubernetes deployments.
>
> Remember, service accounts are a critical security component, so it's important to regularly test and review their configuration to prevent unauthorized access and potential security breaches.
cross-posted from: https://lemmy.run/post/10206
> # Creating a Helm Chart for Kubernetes
>
> In this tutorial, we will learn how to create a Helm chart for deploying applications on Kubernetes. Helm is a package manager for Kubernetes that simplifies the deployment and management of applications. By using Helm charts, you can define and version your application deployments as reusable templates.
>
> ## Prerequisites
>
> Before we begin, make sure you have the following prerequisites installed:
>
> - Helm: Follow the official Helm documentation for installation instructions.
>
> ## Step 1: Initialize a Helm Chart
>
> To start creating a Helm chart, open a terminal and navigate to the directory where you want to create your chart. Then, run the following command:
>
> shell > helm create my-chart >
>
> This will create a new directory named my-chart with the basic structure of a Helm chart.
>
> ## Step 2: Customize the Chart
>
> Inside the my-chart directory, you will find several files and directories. The most important ones are:
>
> - Chart.yaml: This file contains metadata about the chart, such as its name, version, and dependencies.
> - values.yaml: This file defines the default values for the configuration options used in the chart.
> - templates/: This directory contains the template files for deploying Kubernetes resources.
>
> You can customize the chart by modifying these files and adding new ones as needed. For example, you can update the Chart.yaml file with your desired metadata and edit the values.yaml file to set default configuration values.
>
> ## Step 3: Define Kubernetes Resources
>
> To deploy your application on Kubernetes, you need to define the necessary Kubernetes resources in the templates/ directory. Helm uses the Go template language to generate Kubernetes manifests from these templates.
>
> For example, you can create a deployment.yaml template to define a Kubernetes Deployment:
>
> yaml > apiVersion: apps/v1 > kind: Deployment > metadata: > name: {{ .Release.Name }}-deployment > spec: > replicas: {{ .Values.replicaCount }} > template: > metadata: > labels: > app: {{ .Release.Name }} > spec: > containers: > - name: {{ .Release.Name }} > image: {{ .Values.image.repository }}:{{ .Values.image.tag }} > ports: > - containerPort: {{ .Values.containerPort }} >
>
> This template uses the values defined in values.yaml to customize the Deployment's name, replica count, image, and container port.
>
> ## Step 4: Package and Install the Chart
>
> Once you have defined your Helm chart and customized the templates, you can package and install it on a Kubernetes cluster. To package the chart, run the following command:
>
> shell > helm package my-chart >
>
> This will create a .tgz file containing the packaged chart.
>
> To install the chart on a Kubernetes cluster, use the following command:
>
> shell > helm install my-release my-chart-0.1.0.tgz >
>
> Replace my-release with the desired release name and my-chart-0.1.0.tgz with the name of your packaged chart.
>
> ## Conclusion
>
> Congratulations! You have learned how to create a Helm chart for deploying applications on Kubernetes. By leveraging Helm's package management capabilities, you can simplify the deployment and management of your Kubernetes-based applications.
>
> Feel free to explore the Helm documentation for more advanced features and best practices.
>
> Happy charting!
cross-posted from: https://lemmy.run/post/10475
> ## Testing Service Accounts in Kubernetes
>
> Service accounts in Kubernetes are used to provide a secure way for applications and services to authenticate and interact with the Kubernetes API. Testing service accounts ensures their functionality and security. In this guide, we will explore different methods to test service accounts in Kubernetes.
>
> ### 1. Verifying Service Account Existence
>
> To start testing service accounts, you first need to ensure they exist in your Kubernetes cluster. You can use the following command to list all the available service accounts:
>
> bash > kubectl get serviceaccounts >
>
> Verify that the service account you want to test is present in the output. If it's missing, you may need to create it using a YAML manifest or the kubectl create serviceaccount command.
>
> ### 2. Checking Service Account Permissions
>
> After confirming the existence of the service account, the next step is to verify its permissions. Service accounts in Kubernetes are associated with roles or cluster roles, which define what resources and actions they can access.
>
> To check the permissions of a service account, you can use the kubectl auth can-i command. For example, to check if a service account can create pods, run:
>
> bash > kubectl auth can-i create pods --as=system:serviceaccount:<namespace>:<service-account> >
>
> Replace <namespace> with the desired namespace and <service-account> with the name of the service account.
>
> ### 3. Testing Service Account Authentication
>
> Service accounts authenticate with the Kubernetes API using bearer tokens. To test service account authentication, you can manually retrieve the token associated with the service account and use it to authenticate requests.
>
> To get the token for a service account, run:
>
> bash > kubectl get secret <service-account-token-secret> -o jsonpath="{.data.token}" | base64 --decode >
>
> Replace <service-account-token-secret> with the actual name of the secret associated with the service account. This command decodes and outputs the service account token.
>
> You can then use the obtained token to authenticate requests to the Kubernetes API, for example, by including it in the Authorization header using tools like curl or writing a simple program.
>
> ### 4. Testing Service Account RBAC Policies
>
> Role-Based Access Control (RBAC) policies govern the access permissions for service accounts. It's crucial to test these policies to ensure service accounts have the appropriate level of access.
>
> One way to test RBAC policies is by creating a Pod that uses the service account you want to test and attempting to perform actions that the service account should or shouldn't be allowed to do. Observe the behavior and verify if the access is granted or denied as expected.
>
> ### 5. Automated Testing
>
> To streamline the testing process, you can create automated tests using testing frameworks and tools specific to Kubernetes. For example, the Kubernetes Test Framework (KTF) provides a set of libraries and utilities for writing tests for Kubernetes components, including service accounts.
>
> Using such frameworks allows you to write comprehensive test cases to validate service account behavior, permissions, and RBAC policies automatically.
>
> ### Conclusion
>
> Testing service accounts in Kubernetes ensures their proper functioning and adherence to security policies. By verifying service account existence, checking permissions, testing authentication, and validating RBAC policies, you can confidently use and rely on service accounts in your Kubernetes deployments.
>
> Remember, service accounts are a critical security component, so it's important to regularly test and review their configuration to prevent unauthorized access and potential security breaches.
cross-posted from: https://lemmy.run/post/10475
> ## Testing Service Accounts in Kubernetes
>
> Service accounts in Kubernetes are used to provide a secure way for applications and services to authenticate and interact with the Kubernetes API. Testing service accounts ensures their functionality and security. In this guide, we will explore different methods to test service accounts in Kubernetes.
>
> ### 1. Verifying Service Account Existence
>
> To start testing service accounts, you first need to ensure they exist in your Kubernetes cluster. You can use the following command to list all the available service accounts:
>
> bash > kubectl get serviceaccounts >
>
> Verify that the service account you want to test is present in the output. If it's missing, you may need to create it using a YAML manifest or the kubectl create serviceaccount command.
>
> ### 2. Checking Service Account Permissions
>
> After confirming the existence of the service account, the next step is to verify its permissions. Service accounts in Kubernetes are associated with roles or cluster roles, which define what resources and actions they can access.
>
> To check the permissions of a service account, you can use the kubectl auth can-i command. For example, to check if a service account can create pods, run:
>
> bash > kubectl auth can-i create pods --as=system:serviceaccount:<namespace>:<service-account> >
>
> Replace <namespace> with the desired namespace and <service-account> with the name of the service account.
>
> ### 3. Testing Service Account Authentication
>
> Service accounts authenticate with the Kubernetes API using bearer tokens. To test service account authentication, you can manually retrieve the token associated with the service account and use it to authenticate requests.
>
> To get the token for a service account, run:
>
> bash > kubectl get secret <service-account-token-secret> -o jsonpath="{.data.token}" | base64 --decode >
>
> Replace <service-account-token-secret> with the actual name of the secret associated with the service account. This command decodes and outputs the service account token.
>
> You can then use the obtained token to authenticate requests to the Kubernetes API, for example, by including it in the Authorization header using tools like curl or writing a simple program.
>
> ### 4. Testing Service Account RBAC Policies
>
> Role-Based Access Control (RBAC) policies govern the access permissions for service accounts. It's crucial to test these policies to ensure service accounts have the appropriate level of access.
>
> One way to test RBAC policies is by creating a Pod that uses the service account you want to test and attempting to perform actions that the service account should or shouldn't be allowed to do. Observe the behavior and verify if the access is granted or denied as expected.
>
> ### 5. Automated Testing
>
> To streamline the testing process, you can create automated tests using testing frameworks and tools specific to Kubernetes. For example, the Kubernetes Test Framework (KTF) provides a set of libraries and utilities for writing tests for Kubernetes components, including service accounts.
>
> Using such frameworks allows you to write comprehensive test cases to validate service account behavior, permissions, and RBAC policies automatically.
>
> ### Conclusion
>
> Testing service accounts in Kubernetes ensures their proper functioning and adherence to security policies. By verifying service account existence, checking permissions, testing authentication, and validating RBAC policies, you can confidently use and rely on service accounts in your Kubernetes deployments.
>
> Remember, service accounts are a critical security component, so it's important to regularly test and review their configuration to prevent unauthorized access and potential security breaches.
cross-posted from: https://lemmy.run/post/10206
> # Creating a Helm Chart for Kubernetes
>
> In this tutorial, we will learn how to create a Helm chart for deploying applications on Kubernetes. Helm is a package manager for Kubernetes that simplifies the deployment and management of applications. By using Helm charts, you can define and version your application deployments as reusable templates.
>
> ## Prerequisites
>
> Before we begin, make sure you have the following prerequisites installed:
>
> - Helm: Follow the official Helm documentation for installation instructions.
>
> ## Step 1: Initialize a Helm Chart
>
> To start creating a Helm chart, open a terminal and navigate to the directory where you want to create your chart. Then, run the following command:
>
> shell > helm create my-chart >
>
> This will create a new directory named my-chart with the basic structure of a Helm chart.
>
> ## Step 2: Customize the Chart
>
> Inside the my-chart directory, you will find several files and directories. The most important ones are:
>
> - Chart.yaml: This file contains metadata about the chart, such as its name, version, and dependencies.
> - values.yaml: This file defines the default values for the configuration options used in the chart.
> - templates/: This directory contains the template files for deploying Kubernetes resources.
>
> You can customize the chart by modifying these files and adding new ones as needed. For example, you can update the Chart.yaml file with your desired metadata and edit the values.yaml file to set default configuration values.
>
> ## Step 3: Define Kubernetes Resources
>
> To deploy your application on Kubernetes, you need to define the necessary Kubernetes resources in the templates/ directory. Helm uses the Go template language to generate Kubernetes manifests from these templates.
>
> For example, you can create a deployment.yaml template to define a Kubernetes Deployment:
>
> yaml > apiVersion: apps/v1 > kind: Deployment > metadata: > name: {{ .Release.Name }}-deployment > spec: > replicas: {{ .Values.replicaCount }} > template: > metadata: > labels: > app: {{ .Release.Name }} > spec: > containers: > - name: {{ .Release.Name }} > image: {{ .Values.image.repository }}:{{ .Values.image.tag }} > ports: > - containerPort: {{ .Values.containerPort }} >
>
> This template uses the values defined in values.yaml to customize the Deployment's name, replica count, image, and container port.
>
> ## Step 4: Package and Install the Chart
>
> Once you have defined your Helm chart and customized the templates, you can package and install it on a Kubernetes cluster. To package the chart, run the following command:
>
> shell > helm package my-chart >
>
> This will create a .tgz file containing the packaged chart.
>
> To install the chart on a Kubernetes cluster, use the following command:
>
> shell > helm install my-release my-chart-0.1.0.tgz >
>
> Replace my-release with the desired release name and my-chart-0.1.0.tgz with the name of your packaged chart.
>
> ## Conclusion
>
> Congratulations! You have learned how to create a Helm chart for deploying applications on Kubernetes. By leveraging Helm's package management capabilities, you can simplify the deployment and management of your Kubernetes-based applications.
>
> Feel free to explore the Helm documentation for more advanced features and best practices.
>
> Happy charting!
cross-posted from: https://lemmy.run/post/10044
> # Beginner's Guide to nc (Netcat)
>
> Welcome to the beginner's guide to nc (Netcat)! Netcat is a versatile networking utility that allows you to read from and write to network connections using TCP or UDP. It's a powerful tool for network troubleshooting, port scanning, file transfer, and even creating simple network servers. In this guide, we'll cover the basics of nc and how to use it effectively.
>
> ## Installation
>
> To use nc, you first need to install it on your system. The installation process may vary depending on your operating system. Here are a few common methods:
>
> ### Linux
>
> On most Linux distributions, nc is usually included by default. If it's not installed, you can install it using your package manager. For example, on Ubuntu or Debian, open a terminal and run:
>
> > sudo apt-get install netcat >
>
> ### macOS
>
> macOS doesn't come with nc pre-installed, but you can easily install it using the Homebrew package manager. Open a terminal and run:
>
> > brew install netcat >
>
> ### Windows
>
> For Windows users, you can download the official version of nc from the Nmap project's website. Choose the appropriate installer for your system and follow the installation instructions.
>
> ## Basic Usage
>
> Once you have nc installed, you can start using it to interact with network connections. Here are a few common use cases:
>
> ### Connect to a Server
>
> To connect to a server using nc, you need to know the server's IP address or domain name and the port number it's listening on. Use the following command:
>
> > nc <host> <port> >
>
> For example, to connect to a web server running on example.com on port 80, you would run:
>
> > nc example.com 80 >
>
> ### Send and Receive Data
>
> After establishing a connection, you can send and receive data through nc. Anything you type will be sent to the server, and any response from the server will be displayed on your screen. Simply type your message and press Enter.
>
> ### File Transfer
>
> nc can also be used for simple file transfer between two machines. One machine acts as the server and the other as the client. On the receiving machine (server), run the following command:
>
> > nc -l <port> > output_file >
>
> On the sending machine (client), use the following command to send a file:
>
> > nc <server_ip> <port> < input_file >
>
> The receiving machine will save the file as output_file. Make sure to replace <port>, <server_ip>, input_file, and output_file with the appropriate values.
>
> ### Port Scanning
>
> Another useful feature of nc is port scanning. It allows you to check if a particular port on a remote machine is open or closed. Use the following command:
>
> > nc -z <host> <start_port>-<end_port> >
>
> For example, to scan ports 1 to 100 on example.com, run:
>
> > nc -z example.com 1-100 >
>
> ## Conclusion
>
> Congratulations! You've learned the basics of nc and how to use it for various network-related tasks. This guide only scratches the surface of nc's capabilities, so feel free to explore more advanced features and options in the official documentation or online resources. Happy networking!
cross-posted from: https://lemmy.run/post/10044
> # Beginner's Guide to nc (Netcat)
>
> Welcome to the beginner's guide to nc (Netcat)! Netcat is a versatile networking utility that allows you to read from and write to network connections using TCP or UDP. It's a powerful tool for network troubleshooting, port scanning, file transfer, and even creating simple network servers. In this guide, we'll cover the basics of nc and how to use it effectively.
>
> ## Installation
>
> To use nc, you first need to install it on your system. The installation process may vary depending on your operating system. Here are a few common methods:
>
> ### Linux
>
> On most Linux distributions, nc is usually included by default. If it's not installed, you can install it using your package manager. For example, on Ubuntu or Debian, open a terminal and run:
>
> > sudo apt-get install netcat >
>
> ### macOS
>
> macOS doesn't come with nc pre-installed, but you can easily install it using the Homebrew package manager. Open a terminal and run:
>
> > brew install netcat >
>
> ### Windows
>
> For Windows users, you can download the official version of nc from the Nmap project's website. Choose the appropriate installer for your system and follow the installation instructions.
>
> ## Basic Usage
>
> Once you have nc installed, you can start using it to interact with network connections. Here are a few common use cases:
>
> ### Connect to a Server
>
> To connect to a server using nc, you need to know the server's IP address or domain name and the port number it's listening on. Use the following command:
>
> > nc <host> <port> >
>
> For example, to connect to a web server running on example.com on port 80, you would run:
>
> > nc example.com 80 >
>
> ### Send and Receive Data
>
> After establishing a connection, you can send and receive data through nc. Anything you type will be sent to the server, and any response from the server will be displayed on your screen. Simply type your message and press Enter.
>
> ### File Transfer
>
> nc can also be used for simple file transfer between two machines. One machine acts as the server and the other as the client. On the receiving machine (server), run the following command:
>
> > nc -l <port> > output_file >
>
> On the sending machine (client), use the following command to send a file:
>
> > nc <server_ip> <port> < input_file >
>
> The receiving machine will save the file as output_file. Make sure to replace <port>, <server_ip>, input_file, and output_file with the appropriate values.
>
> ### Port Scanning
>
> Another useful feature of nc is port scanning. It allows you to check if a particular port on a remote machine is open or closed. Use the following command:
>
> > nc -z <host> <start_port>-<end_port> >
>
> For example, to scan ports 1 to 100 on example.com, run:
>
> > nc -z example.com 1-100 >
>
> ## Conclusion
>
> Congratulations! You've learned the basics of nc and how to use it for various network-related tasks. This guide only scratches the surface of nc's capabilities, so feel free to explore more advanced features and options in the official documentation or online resources. Happy networking!
Hello r/linuxadmin reddit refugees to c/linuxadmin.
I moved to Lemmy and was missing one of my favorite sub.
After missing it, I decided to create and make it available to others like me.
Welcome all and let's create a healthy environment for discussion and sharing tips.
cross-posted from: https://lemmy.run/post/8710
> # Beginner's Guide to htop
>
> ## Introduction
> htop is an interactive process viewer and system monitor for Linux systems. It provides a real-time overview of your system's processes, resource usage, and other vital system information. This guide will help you get started with htop and understand its various features.
>
> ## Installation
>
> We are assuming that you are using ubuntu or debain based distros here.
>
> To install htop, follow these steps:
>
> 1. Open the terminal.
> 2. Update the package list by running the command: sudo apt update.
> 3. Install htop by running the command: sudo apt install htop.
> 4. Enter your password when prompted.
> 5. Wait for the installation to complete.
>
> ## Launching htop
> Once htop is installed, you can launch it by following these steps:
>
> 1. Open the terminal.
> 2. Type htop and press Enter.
>
> ## Understanding the htop Interface
> After launching htop, you'll see the following information on your screen:
>
> 1. A header displaying the system's uptime, load average, and total number of tasks.
> 2. A list of processes, each represented by a row.
> 3. A footer showing various system-related information.
>
> ## Navigating htop
> htop provides several keyboard shortcuts for navigating and interacting with the interface. Here are some common shortcuts:
>
> - Arrow keys: Move the cursor up and down the process list.
> - Enter: Expand or collapse a process to show or hide its children.
> - Space: Tag or untag a process.
> - F1: Display the help screen with a list of available shortcuts.
> - F2: Change the setup options, such as columns displayed and sorting methods.
> - F3: Search for a specific process by name.
> - F4: Filter the process list by process owner.
> - F5: Tree view - display the process hierarchy as a tree.
> - F6: Sort the process list by different columns, such as CPU usage or memory.
> - F9: Send a signal to a selected process, such as terminating it.
> - F10: Quit htop and exit the program.
>
> ## Customizing htop
> htop allows you to customize its appearance and behavior. You can modify settings such as colors, columns displayed, and more. To access the setup menu, press the F2 key. Here are a few options you can modify:
>
> - Columns: Select which columns to display in the process list.
> - Colors: Customize the color scheme used by htop.
> - Meters: Choose which system meters to display in the header and footer.
> - Sorting: Set the default sorting method for the process list.
>
> ## Exiting htop
> To exit htop and return to the terminal, press the F10 key or simply close the terminal window.
>
> ## Conclusion
> Congratulations! You now have a basic understanding of how to use htop on the Linux bash terminal. With htop, you can efficiently monitor system processes, resource usage, and gain valuable insights into your Linux system. Explore the various features and options available in htop to get the most out of this powerful tool.
>
> Remember, you can always refer to the built-in help screen (F1) for a complete list of available shortcuts and commands.
>
> Enjoy using htop and happy monitoring!
cross-posted from: https://lemmy.run/post/9328
>
> 1. Introduction to awk:
>
> awk is a powerful text processing tool that allows you to manipulate structured data and perform various operations on it. It uses a simple pattern-action paradigm, where you define patterns to match and corresponding actions to be performed.
>
>
> 2. Basic Syntax:
>
> The basic syntax of awk is as follows:
> > awk 'pattern { action }' input_file >
> - The pattern specifies the conditions that must be met for the action to be performed.
> - The action specifies the operations to be carried out when the pattern is matched.
> - The input_file is the file on which you want to perform the awk operation. If not specified, awk reads from standard input.
>
>
> 3. Printing Lines:
>
> To start with, let's see how to print lines in Markdown using awk. Suppose you have a Markdown file named input.md.
> - To print all lines, use the following command:
> > awk '{ print }' input.md >
> - To print lines that match a specific pattern, use:
> > awk '/pattern/ { print }' input.md >
>
> 4. Field Separation:
>
> By default, awk treats each line as a sequence of fields separated by whitespace. You can access and manipulate these fields using the $ symbol.
> - To print the first field of each line, use:
> > awk '{ print $1 }' input.md >
>
> 5. Conditional Statements:
>
> awk allows you to perform conditional operations using if statements.
> - To print lines where a specific field matches a condition, use:
> > awk '$2 == "value" { print }' input.md >
>
> 6. Editing Markdown Files:
>
> Markdown files often contain structured elements such as headings, lists, and links. You can use awk to modify and manipulate these elements.
> - To change all occurrences of a specific word, use the gsub function:
> > awk '{ gsub("old_word", "new_word"); print }' input.md >
>
> 7. Saving Output:
>
> By default, awk prints the result on the console. If you want to save it to a file, use the redirection operator (>).
> - To save the output to a file, use:
> > awk '{ print }' input.md > output.md >
>
> 8. Further Learning:
>
> This guide provides a basic introduction to using awk for text manipulation in Markdown. To learn more advanced features and techniques, refer to the awk documentation and explore additional resources and examples available online.
>
> Remember, awk is a versatile tool, and its applications extend beyond Markdown manipulation. It can be used for various text processing tasks in different contexts.
-
Introduction to
awk:awkis a powerful text processing tool that allows you to manipulate structured data and perform various operations on it. It uses a simple pattern-action paradigm, where you define patterns to match and corresponding actions to be performed. -
Basic Syntax:
The basic syntax of
awkis as follows:awk 'pattern { action }' input_file- The pattern specifies the conditions that must be met for the action to be performed.
- The action specifies the operations to be carried out when the pattern is matched.
- The input_file is the file on which you want to perform the
awkoperation. If not specified,awkreads from standard input.
-
Printing Lines:
To start with, let's see how to print lines in Markdown using
awk. Suppose you have a Markdown file namedinput.md.- To print all lines, use the following command:
awk '{ print }' input.md - To print lines that match a specific pattern, use:
awk '/pattern/ { print }' input.md
- To print all lines, use the following command:
-
Field Separation:
By default,
awktreats each line as a sequence of fields separated by whitespace. You can access and manipulate these fields using the$symbol.- To print the first field of each line, use:
awk '{ print $1 }' input.md
- To print the first field of each line, use:
-
Conditional Statements:
awkallows you to perform conditional operations usingifstatements.- To print lines where a specific field matches a condition, use:
awk '$2 == "value" { print }' input.md
- To print lines where a specific field matches a condition, use:
-
Editing Markdown Files:
Markdown files often contain structured elements such as headings, lists, and links. You can use
awkto modify and manipulate these elements.- To change all occurrences of a specific word, use the
gsubfunction:awk '{ gsub("old_word", "new_word"); print }' input.md
- To change all occurrences of a specific word, use the
-
Saving Output:
By default,
awkprints the result on the console. If you want to save it to a file, use the redirection operator (>).- To save the output to a file, use:
awk '{ print }' input.md > output.md
- To save the output to a file, use:
-
Further Learning:
This guide provides a basic introduction to using
awkfor text manipulation in Markdown. To learn more advanced features and techniques, refer to theawkdocumentation and explore additional resources and examples available online.
Remember, awk is a versatile tool, and its applications extend beyond Markdown manipulation. It can be used for various text processing tasks in different contexts.